lnmp 集成环境: https://lnmp.org
通过 Nginx 日志我们可以看到 Let’s Encrypt 的验证是通过项目根目录下的 .well-known 文件夹,所以我们需要把该目录排除即可。
/home/wwwlogs/sls.hongfs.cn.log
1
2
3
4
| 34.209.232.166 - - [02/Apr/2020:20:27:58 +0800] "GET /.well-known/acme-challenge/MXS_Z0y5XognhDh9U7ib-jf9yyRpKSvrK5kDT5V3lC8 HTTP/1.1" 200 87 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)"
66.133.109.36 - - [02/Apr/2020:20:27:59 +0800] "GET /.well-known/acme-challenge/MXS_Z0y5XognhDh9U7ib-jf9yyRpKSvrK5kDT5V3lC8 HTTP/1.1" 200 87 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)"
3.14.255.131 - - [02/Apr/2020:20:28:00 +0800] "GET /.well-known/acme-challenge/MXS_Z0y5XognhDh9U7ib-jf9yyRpKSvrK5kDT5V3lC8 HTTP/1.1" 200 87 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)"
18.194.58.132 - - [02/Apr/2020:20:28:01 +0800] "GET /.well-known/acme-challenge/MXS_Z0y5XognhDh9U7ib-jf9yyRpKSvrK5kDT5V3lC8 HTTP/1.1" 200 87 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)"
|
/usr/local/nginx/conf/vhost/ssl.hongfs.cn.conf
项目的 Nginx 配置文件,这里只需修改监听 80 端口的配置。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| server
{
listen 80;
#listen [::]:80;
server_name ssl.hongfs.cn ;
index index.html index.htm index.php default.html default.htm default.php;
root /home/wwwroot/ssl.hongfs.cn;
# 非 /.well-known 目录进行跳转到 HTTPS
if ($request_uri !~ /.well-known) {
rewrite ^(.*)$ https://$host$1 permanent;
}
access_log /home/wwwlogs/ssl.hongfs.cn.log;
}
|
修改完配置后记得 重启 相关服务。
测试
强制重新生成
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
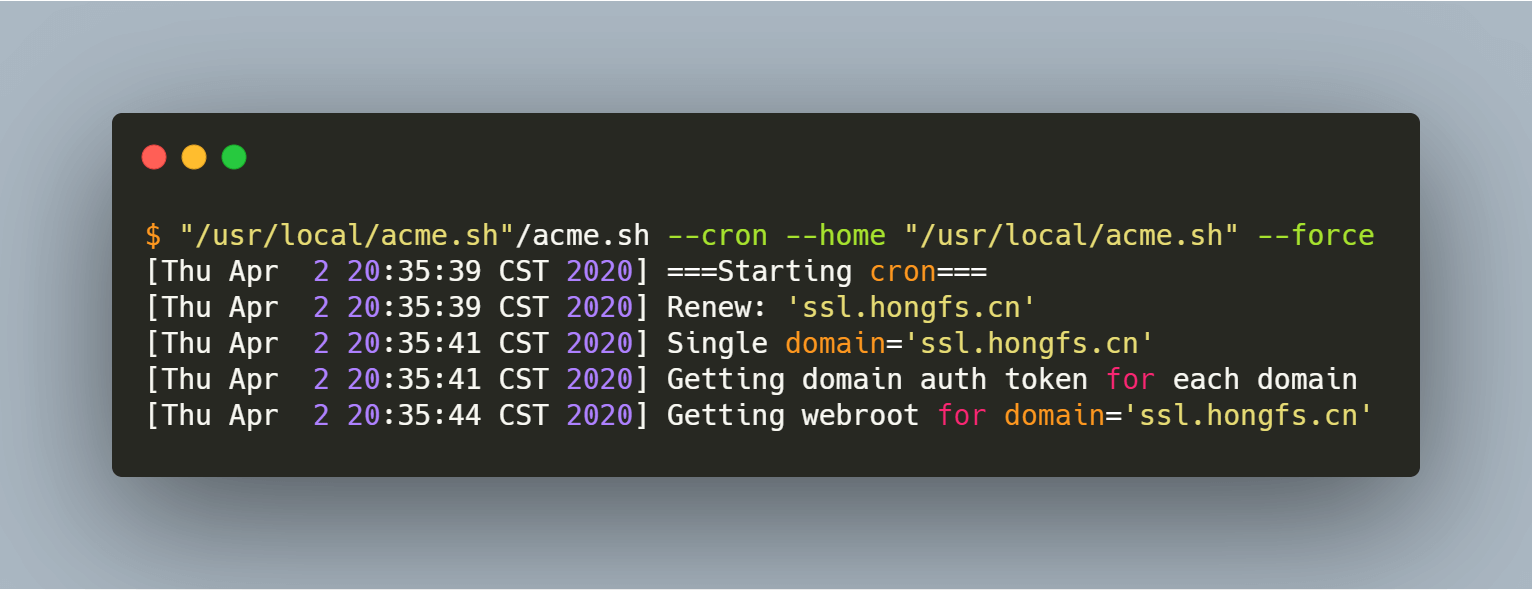
| $ "/usr/local/acme.sh"/acme.sh --cron --home "/usr/local/acme.sh" --force
[Thu Apr 2 20:35:39 CST 2020] ===Starting cron===
[Thu Apr 2 20:35:39 CST 2020] Renew: 'ssl.hongfs.cn'
[Thu Apr 2 20:35:41 CST 2020] Single domain='ssl.hongfs.cn'
[Thu Apr 2 20:35:41 CST 2020] Getting domain auth token for each domain
[Thu Apr 2 20:35:44 CST 2020] Getting webroot for domain='ssl.hongfs.cn'
[Thu Apr 2 20:35:44 CST 2020] ssl.hongfs.cn is already verified, skip http-01.
[Thu Apr 2 20:35:44 CST 2020] Verify finished, start to sign.
[Thu Apr 2 20:35:44 CST 2020] Lets finalize the order, Le_OrderFinalize: https://acme-v02.api.letsencrypt.org/acme/finalize/82290940/2865693058
[Thu Apr 2 20:35:45 CST 2020] Download cert, Le_LinkCert: https://acme-v02.api.letsencrypt.org/acme/cert/03687f02361c1e714f1968819473f65bfd6d
[Thu Apr 2 20:35:46 CST 2020] Cert success.
[Thu Apr 2 20:35:46 CST 2020] Your cert is in /usr/local/nginx/conf/ssl/ssl.hongfs.cn/ssl.hongfs.cn.cer
[Thu Apr 2 20:35:46 CST 2020] Your cert key is in /usr/local/nginx/conf/ssl/ssl.hongfs.cn/ssl.hongfs.cn.key
[Thu Apr 2 20:35:46 CST 2020] The intermediate CA cert is in /usr/local/nginx/conf/ssl/ssl.hongfs.cn/ca.cer
[Thu Apr 2 20:35:46 CST 2020] And the full chain certs is there: /usr/local/nginx/conf/ssl/ssl.hongfs.cn/fullchain.cer
[Thu Apr 2 20:35:46 CST 2020] Run reload cmd: /etc/init.d/nginx reload
Reload nginx... done
[Thu Apr 2 20:35:46 CST 2020] Reload success
[Thu Apr 2 20:35:46 CST 2020] ===End cron===
|
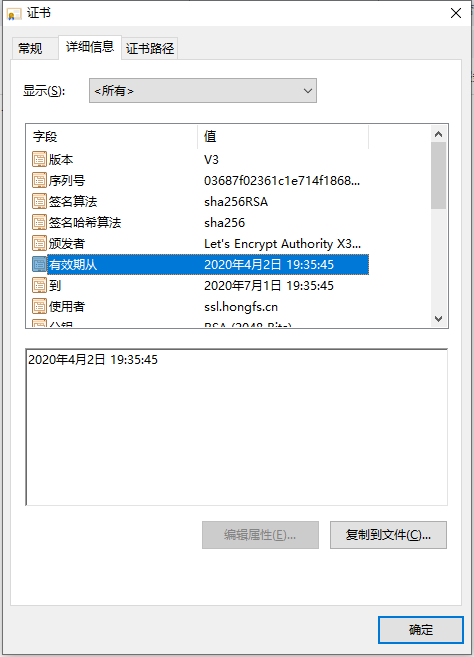
通过浏览器我们可以看到证书的时间更新了,说明成功生成了。